Broker Blog
Stay ahead with our latest Broker Insights and Updates
Update on Signaturgruppen Broker
- February 2025
Read about the latest developments for Signaturgruppen Broker here.
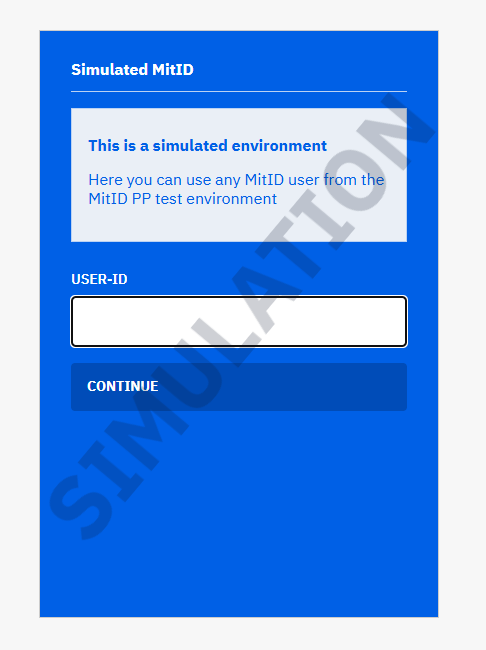
MitID Simulation
The Simulation and Enterprise End-to-End testing functionality in Signaturgruppen Broker provides a robust method for integrating with the broker’s OIDC interface while simulating external dependencies. This feature enables seamless testing and operation in scenarios where external integrations with Signaturgruppen Broker are either offline or not fully functional. By adding the top-level simulation parameter to the broker’s OIDC interface, Signaturgruppen Broker simulates all external integrations, including API calls to MitID and NemLog-In backends in the pre-production environment. This allows developers and businesses to validate their integrations even in offline scenarios.
Key Simulation Features
The simulation functionality offers various modes to accommodate different testing needs. One mode replicates external authentication flows, allowing developers to simulate user interactions as they would occur in a live setup. Another mode bypasses user interface elements entirely, enabling backend process testing and automation without manual input.
Features and Benefits
Simulated External Integrations:
- External systems such as MitID and NemLog-In are fully simulated using realistic data.
- Ensures uptime and enables offline testing without reliance on live services.
Improved Performance:
- Faster than live flows, as obfuscation and waiting times are skipped.
- No user credentials required in simulated setups.
- Efficient troubleshooting and shorter testing cycles.
Reliable and Predictable Testing:
- Stabilized flows ensure consistent and repeatable test scenarios.
- Identical output between live and simulated setups makes integration switching easier.
How It Works
Activating Simulation
Simulation is activated by adding a specific parameter to the OIDC request URL. The system then interprets these parameters to generate the appropriate responses and emulate external authentication systems.
For more information about pricing, contact sales: sales@signaturgruppen.dk
Read more at Simulated MitID Login in Test
___________________________________
Improved App MitID Integration on iOS and Android
We have updated our App MitID integration documentation with new recommendations and examples, making it easier to implement a secure and seamless user experience.
✅ iOS – We now recommend ASWebAuthenticationSession instead of SFSafariViewController, as it provides a better and more secure authentication experience.
✅ Android – We have added an example of how to connect your app with a webpage using the PostMessage API. This ensures that the session is correctly terminated when the login flow is completed.
✅ More flexibility – You can now eliminate unnecessary extra clicks for users and choose whether to handle the authorization code directly in the app or in your backend.
Read the updated documentation here:
___________________________________
Flexible MitID Authentication Without a Browser
We are introducing the MitID Flex App – a solution that enables the use of MitID in situations where a standard browser is unavailable. This unlocks authentication for scenarios such as smart TVs, phone support, and other cases where a traditional login process is not possible.
The MitID Flex App is based on the OIDC Client Initiated Backchannel Authentication (CIBA) standard, ensuring a seamless and secure authentication process. A service can initiate authentication, which is then confirmed in the MitID app on the user’s device. Through an asynchronous authentication flow, the service communicates directly with MitID via Signaturgruppen Broker, ensuring a secure and efficient login experience – even without an active browser.
What Does This Mean for You?
✔ Authentication in scenarios without a browser
✔ Secure MitID login for phone support
✔ Seamless integration via Signaturgruppen Broker
✔ Support for devices without an interactive screen
We have developed an online demo showcasing how the MitID Flex App can be used in a helpdesk scenario. This is just one example – the solution can be tailored to various use cases where standard MitID login is impractical.
Could you benefit from a more flexible authentication solution? Contact us to learn more about how the MitID Flex App and CIBA integration can be implemented in your setup.
___________________________________
New Feature: Upload Your Logo to the MitID App
We have introduced a new feature in our administration portal that makes it easier for service providers to have their logo displayed in the MitID app. This increases user confidence by ensuring a recognizable visual identity when end users swipe to approve transactions.
Why Is This Important?
MitID recommends that service providers upload their logo to help users distinguish between legitimate approval requests and potential fraud attempts. A clear visual identity reduces the risk of phishing and increases user trust in the authentication process.
How It Works
Service providers simply log in to the administration portal – either in PP/test or production. The new feature is available in the left-hand menu. From there, they follow a simple guide to upload their logo as an .svg file.
Our system automatically validates and optimizes the file to comply with MitID’s requirements. Once the logo appears correctly, they can submit the request.
Our support team reviews and approves the request within 1-2 business days. Once approved, the logo will be displayed in the MitID app when users swipe to confirm.
By uploading a logo, you not only strengthen your brand but also contribute to a more secure authentication experience for your users.
Do you have questions or are unsure whether you have access to the administration portal? Contact our support team at support@signaturgruppen.dk
___________________________________
Enhanced Security with Pushed Authorization Request (PAR)
Pushed Authorization Request (PAR) is a critical security enhancement in the OAuth 2.0 and OpenID Connect (OIDC) frameworks, improving the security and reliability of authorization requests. Instead of sending authorization parameters through the user’s browser, PAR allows clients to send these parameters directly to the authorization server, reducing risks and providing better control.
Why Use PAR?
- Stronger Security: PAR eliminates the need to send sensitive data (e.g., redirect_uri, scopes) via the front channel, reducing the risk of request manipulation or data leakage in browser history.
- Pre-validation of Requests: The authorization server can validate parameters before the user initiates the authorization process, ensuring consistency and reducing errors.
- Support for Complex Requests: PAR makes it easier to handle large or complex requests, including JSON Web Tokens (JWTs) and encrypted data.
How PAR Works
-
The service provider sends the authorization request
The service provider sends a POST request to the PAR endpoint with all authorization parameters. -
The authorization server returns a request_uri
The server validates the request and returns a unique request_uri that refers to the pre-validated request. -
The user initiates authorization
The user is redirected to the authorization endpoint and uses the request_uri instead of sending the parameters directly. -
The server retrieves parameters and processes the request
The authorization server fetches the pre-validated parameters and continues the authorization flow or issues a token.
Benefits of PAR
✅ Higher Security – Protects sensitive data from exposure in the user’s browser.
✅ Improved Error Handling – Detects errors early in the process, reducing failed authorizations.
✅ Compliance with Security Standards – Ensures that sensitive authorization data is handled according to best practices and regulatory requirements.
PAR is already available and free for all customers.
Do you want to strengthen your security setup? Contact us to learn more about integrating PAR into your solution.
Update on: Signaturgruppen Broker
- July 2024
Progress with implementing MitID is advancing. Below you can read about the latest developments.
Age Verification
Denmark leads the EU in age verification for customers purchasing alcohol. Signaturgruppen can provide solutions directly with MitID, as well as more GDPR-friendly options where minimal user information is obtained while still complying with regulations. Read more at MitID Age Verification.
MitID Update
On June 26th, MitID updated the pre-production environment from v13 to v14. Unfortunately, this caused disruptions in the environment. If you experience disruptions either in production or in PP, we recommend following our operational status page: Operational Status, where we will communicate disturbances or announce updates.
The corresponding release is scheduled for August 14th in the production environment. It is not expected that the update will pose challenges for service providers as it primarily includes user-focused changes.
Danish Chamber of Commerce & Signaturgruppen Present:
Webinar on Age Verification for Online Sales
Learn how your online store can comply with new legal requirements for remote sales of alcohol, nicotine, and tobacco with MitID Age Verification. Sign up here.
New Website
We have refreshed our website with a more contemporary look. Alongside this update, we have refined our messaging to ensure our customers can easily and quickly understand our services. Likewise, we have phased out references to Nets in our product names – for example, "Signaturgruppen Broker."
Take a look at the page here.
New Documentation Site
At the same time, we have given our documentation a brush-up and transitioned it from documents to a web format. If you wish to explore our technical integrations, please refer to the Broker Technical Documentation.
Infrastructure Update
Our ongoing efforts to enhance our service necessitate a fundamental update this time around. Most customers will not be affected, but if, for example, you rely on filtering incoming traffic from our data centers, you should update your inbound firewall rule, as indicated below:
Pre-Production (PP)
For PP customers, please note that the source IP address for pp.netseidbroker.dk will change from 91.102.27.1 to an address in subnet 185.208.80.0/22. The update is expected to be completed by August 15th.
Production
For production customers, our source IP for netseidbroker.dk is currently 185.208.81.220 and 185.208.81.236. This is not expected to change immediately, but customers are encouraged to update inbound firewall rules to allow traffic from the 185.208.80.0/22 subnet. The production upgrade is expected to be completed August 25th at 23:00. Please continue to monitor our StatusPage as usual.
Finally, note that during the autumn, we will similarly change the DNS for our service, but customers will have a longer deadline to make this change, and there will be an opportunity for parallel operation.
CPR Match for Qualified Signatures
Nemlog-in was updated to v9 earlier this May. As a result, it is now finally possible to match a private individual with the identity indicated by their signature. This functionality is also available to the service providers we assist with qualified signing.
Read more about the feature here.
Update on: Signaturgruppen Broker
- January 2024
Broker TLS/SSL Server Certificate Chain
Endpoints at MitID and Signaturgruppen Broker are protected with TLS/SSL using server certificates issued by Let's Encrypt.
Previously, the certificate chain presented was, for example, <netseidbroker.dk> -> R3 -> ISRG Root X1
From February 8th onwards, new certificates will be issued and presented exclusively with the chain <netseidbroker.dk> -> R3 The issuing CA 'R3' is issued by 'ISRG Root X1' and is in the trust store of all modern devices. Therefore, it is expected that this change will not cause issues. However, as there may be integrations that do not have correct/updated trust in their keystores or may not support this automatically, we are conducting a controlled update/rollout of new certificates for all PP endpoints on Wednesday, January 17th. Production will follow from February 8th.
As a service provider, you should verify that your integration continues to function in the PP environment after January 18th to ensure there will be no issues for the corresponding integration in production.
MitID v13 Deployment
MitID has scheduled the upcoming update of its infrastructure to v13. Details of the update will be released in the near future. It is not expected that MitID v13 will require action from service providers, but will simply include improvements and functionality related to users.
For precautionary measures, all service providers are encouraged to ensure their integrations work in PP after the update on January 30th, 2024.
The update is scheduled to go into production on February 20th, 2024.
For further updates, please monitor our status page.
Update on: Signaturgruppen Broker
- October 2023
NemID Shutdown - Service Providers to Bid Farewell to NemID
Over time, Signaturgruppen has assisted many service providers in implementing NemID login capabilities. We have also helped many of these providers transition to MitID, supporting both NemID and MitID through our broker.
It has been announced that NemID will shut down on October 31, 2023, with MitID being the future solution moving forward.
For service providers wishing to maintain control over the NemID shutdown, we recommend disabling NemID on their services themselves. If using our broker, you can adjust the IdP configuration in the administration panel or manage it from your application by ensuring the idp_values do not include NemID.
For service providers using our broker for NemID, after the shutdown at the end of October, we will automatically block NemID to ensure it does not initiate, whether configured or requested explicitly with idp_values. This measure aims to ensure a smooth user experience throughout the shutdown period.
Furthermore, we do not anticipate any disruptions to service operations on Signaturgruppen Broker due to the NemID shutdown.
MitID v12 Deployment on October 17th
MitID has announced the deployment of MitID v12 starting on October 17th at 02:00 CET. We do not expect this update to pose challenges for service providers as it primarily includes optimizations and enhancements relevant to users and their registrations.
However, please note that disruption of MitID services of up to 30 minutes is expected starting from 02:10.
Service Provider-Specific Logo in MitID App
MitID recommends that service providers take advantage of the opportunity to integrate a service provider-specific logo into the MitID app. This ensures strong continuity of the service provider's branding and enhances security by allowing users to visually confirm that the transaction being approved is as expected.
We have integrated a validator to easily ensure that an SVG-format logo meets MitID's technical guidelines. The validator is accessible to service providers through the administration portal. From there, simply submit the file to our support team for final configuration in MitID.